Whitelisting: What It Is and How to Whitelist Email Senders ?
This article will analyze the nitty-gritty of whitelisting, including the different types and how it's used for email management. Hint: you won't miss any more important email updates!
Did you know that a cyber attack occurs every 39 seconds? That's why it's important that individuals and organizations reinforce their e-armour for cybersecurity. Creating blacklists, installing malware protection, and setting up spam filters are some of the more effective guards against hackers. However, these safety features sometimes work too well, which means you could miss important emails or lose contact with apps and senders you need.
Is there a way to protect your cyber presence and valuable data without locking everything up in a panic room? There sure is - whitelisting.
Keep reading to learn how to set up your lists of trusted senders, apps, and users!
What Is a Whitelist?
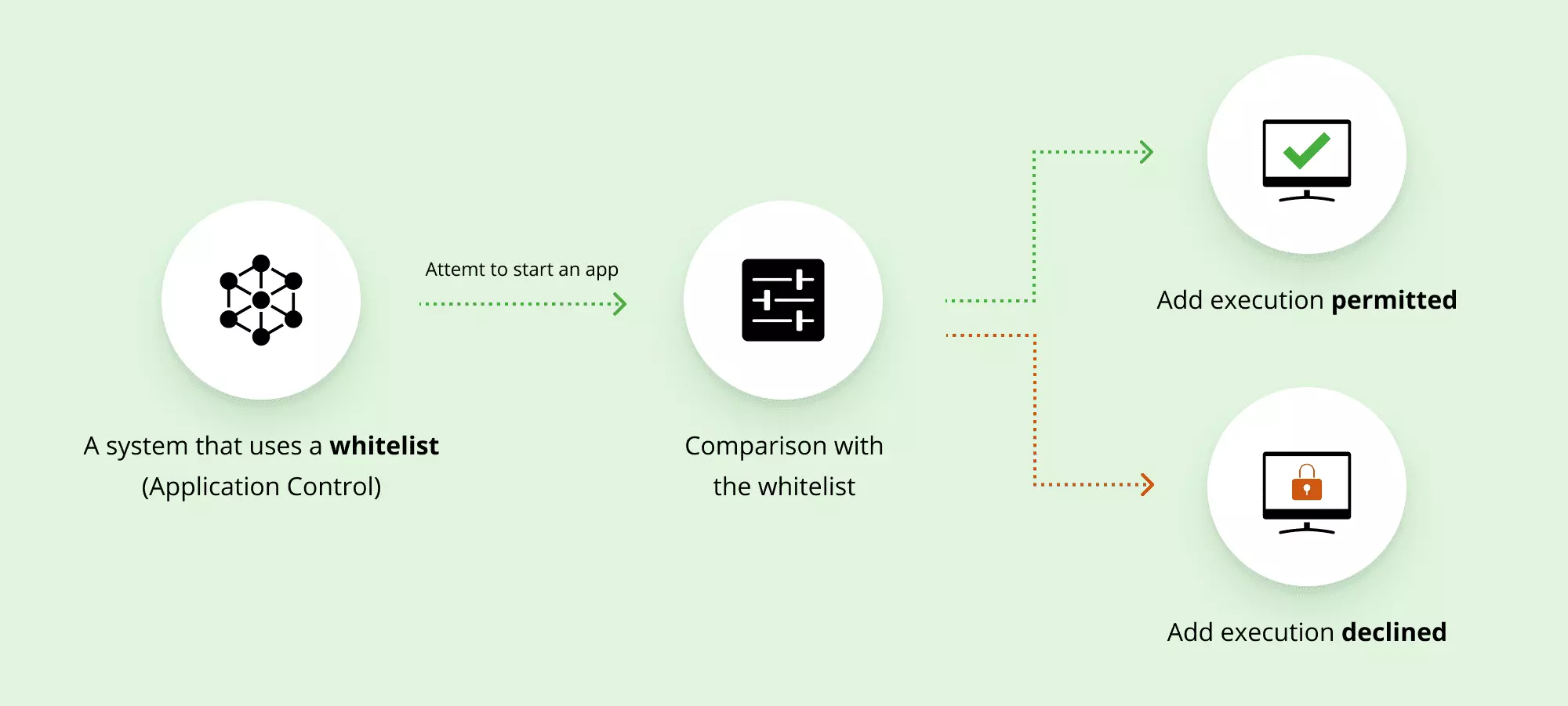
A whitelist is a list of entities that have the green light to communicate with you and your infrastructure.
There is email, IP, and application whitelisting. While whitelisting is a more secure approach than blacklisting, it has its disadvantages.
Here's a breakdown of the pros and cons of whitelists:
|
Pros |
Cons |
|
Strict access control |
Difficult to compile a list |
|
Reduced risk of malicious intent |
Administrative burden of updating the list |
|
Increased safety of internet-connected systems |
Limited creativity and access to tools used to complete tasks |
|
Ability to define what an app or service can and can't do within your system |
Risk of blocking wanted traffic |
For individuals and companies that need high levels of information security, whitelists are a safe choice. They will deny all access except for what is explicitly allowed. And remember, your malware protection is still up and running while a whitelist does its job.
Whitelist vs. Blacklist
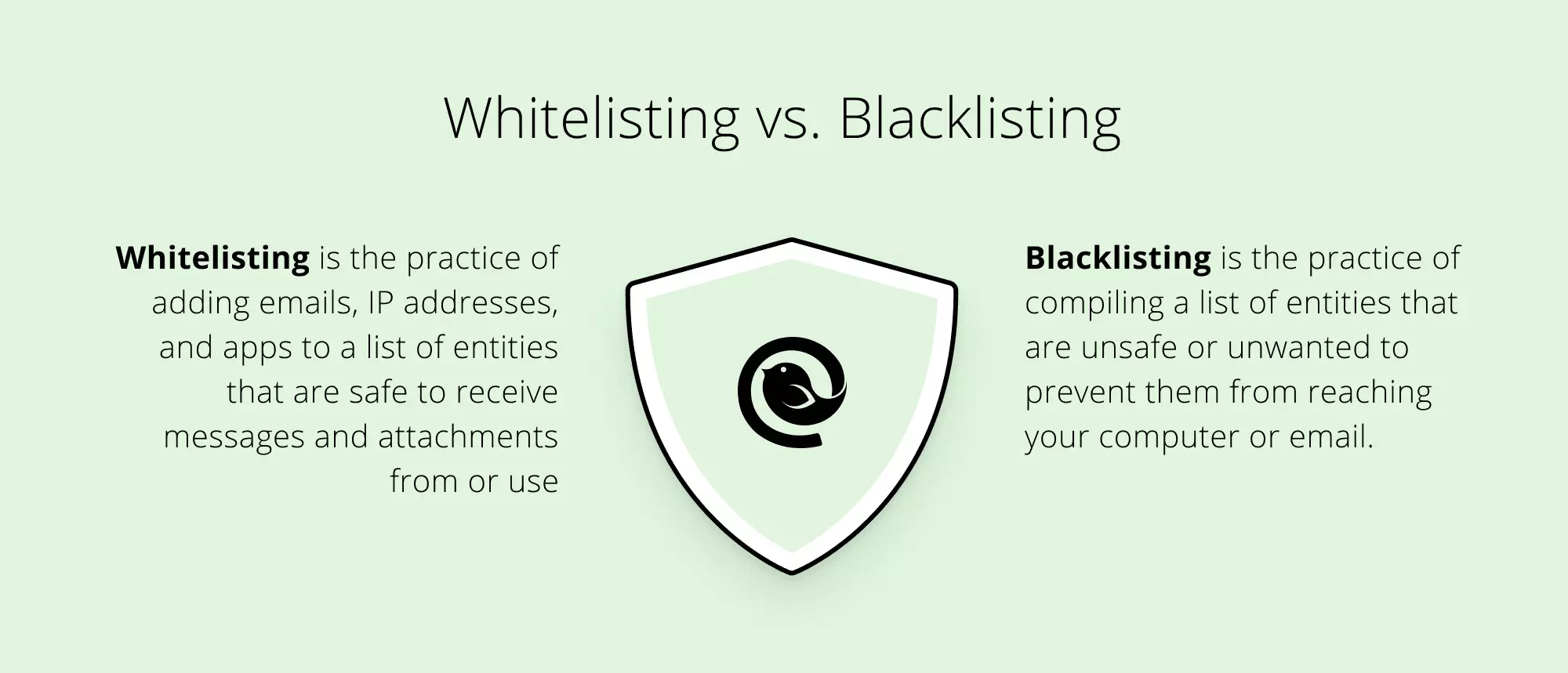
As security measures, both whitelists and blacklists are useful tools. The difference is, whitelisted entities are allowed to communicate with the users' systems, while blacklisted ones are denied that privilege.
Both lists can be used to manage apps, email and IP addresses, websites, domains, organizations, and processes. No matter what approach you choose, you can control which entities can launch, be opened, or send information to you.
By default, security tools such as firewalls, antivirus programs, and spam filters function as blacklists, blocking unwanted content.
Here's an overview of the main differences:
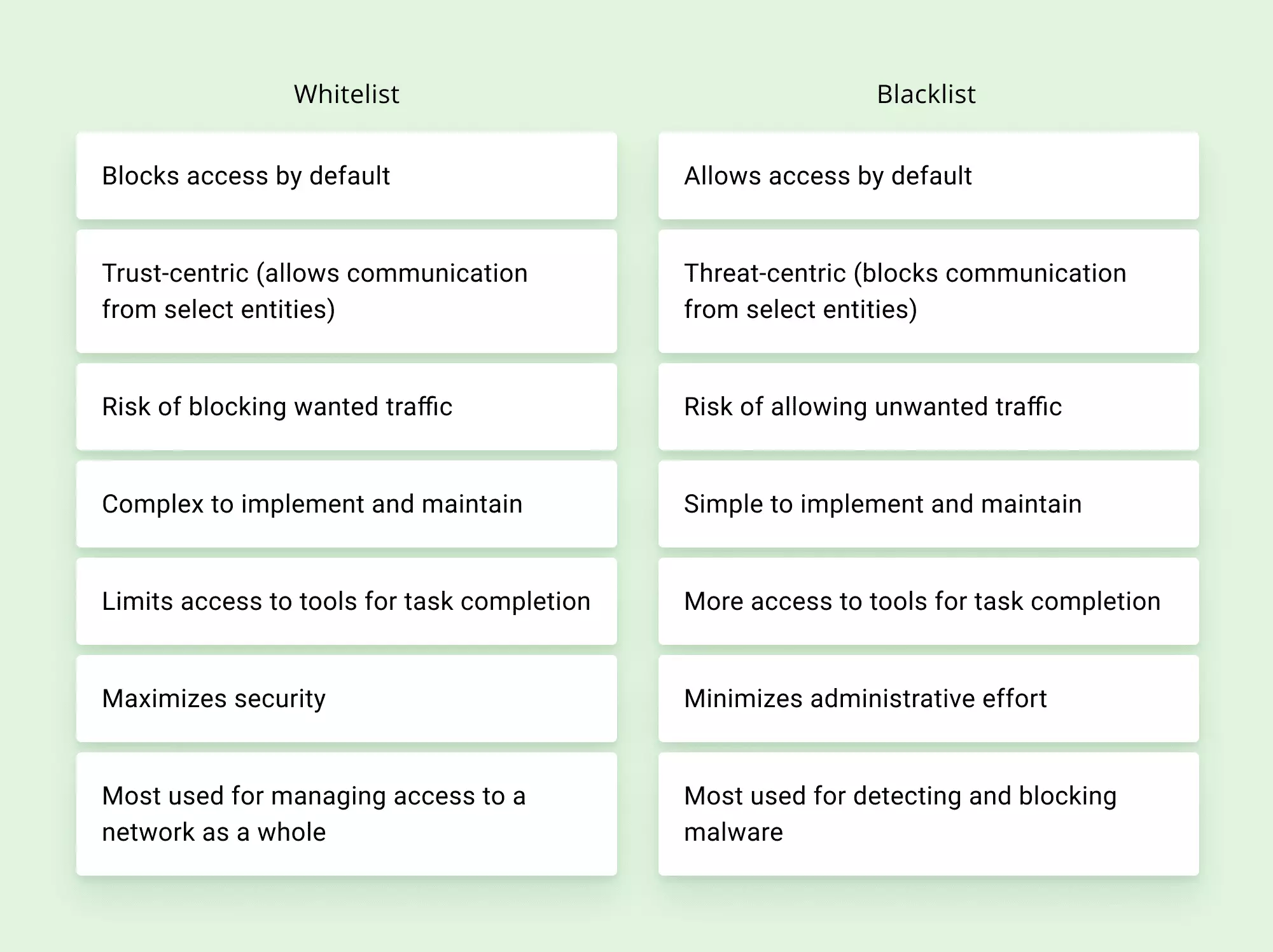
As you can see, both blacklists and whitelists have their benefits and downsides. Choosing the best approach depends on your personal or organization's needs. Using these two strategies together to get the best of both worlds is also a good option.
For individuals and companies that need high levels of information security, whitelists are a safe choice. They will deny all access except for what is explicitly allowed. Implementing a comprehensive operational risk management process alongside whitelisting can further enhance security measures and mitigate potential risks.
How Do Emails Relate to Whitelisting
As mentioned above, you can manage the network and device access for various entities. However, the most commonly used are application, IP address, and email whitelisting.
The Types: IP Addresses, Emails, and Application Whitelisting
In the context of applications, the practice means that only certain apps are allowed to run on a protected device. It's useful for blocking different types of malware, as well as insecure or unlicensed programs.
When choosing which users can access your website or network, creating a list of allowed IP addresses is a common option. This can be done manually or by using a plugin.
Email whitelisting is a way—sometimes the only surefire one—to make sure emails, replies, and attachments from trusted senders always end up in your inbox, where you can see them.
Why You Should Create Email Whitelists
Email clients nowadays automatically sort incoming messages. While this feature can help sort incoming mail by relevance, mistakes do happen. There's nothing more frustrating than waiting for important job-related updates, only to later find out it has been sitting in the wrong tab for days.
To make matters worse, updates to spam filters can create new sets of problems. It's one thing for a message from a new contact to end up in spam, but when a message from a person you've previously conversed with ends up there, it brings a new set of problems. Firstly, it's not something you would expect to happen. And as an email user, you would have to adopt the habit of scanning the spam folder as frequently as the inbox. Secondly, you could miss an important event or your contact could be offended or concerned when you don't respond.
Three Ways to Green-light Email Addresses
Once you've identified the problem, it seems like an easy fix. When you find a message that you want to remove from spam, you'll be prompted to click the "Report not spam" button or similar. You'd think the future messages from this sender would finally go straight to your inbox. Unfortunately, this doesn't solve the problem every time.
This is where an approved senders list comes into play. A sender can end up on an email safelist in three ways.
- The recipient adds them to the trusted senders list. This approach often requires creating a rule or filter (depending on your provider) for the email addresses you trust. Then, you would set the filtering option to "Never send to spam."
- You apply to a whitelist operated by internet service providers, non-profit organizations, or other parties.
- Any sender can pay a fee to be included on a commercial safe senders list operated by an internet service provider. The third way is often used by businesses that need to bypass spam filters to communicate with their customers.
How to Whitelist Emails in Gmail and Other Email Providers
Email clients such as Gmail, Outlook, and others are constantly improving their algorithms for sorting incoming correspondence. While the goal is to improve your productivity and save time, the opposite can happen.
To ensure important communication lands in your main inbox, you need to be proactive. The most efficient way to do this is to manually add whitelisted senders.
How to Whitelist an Email in Gmail
There are several ways to whitelist emails in Gmail.
1. Add a sender to contacts.
If you've already received an email from the person, they will be automatically added to contacts unless you disable this feature. If you're expecting someone to message you, sign into Google Contacts and add the sender manually.
2. Locate the messages you want to always go to your inbox.
Once you open the email, go to options and select "Filter messages like these." The sender information will be pre-filled. You can add more senders or click "Create filter", then "Never send it to spam." You can also mark the conversation as important and categorize the message so it goes to your "Primary" tab or wherever you want to send similar messages. Another way is to drag the message to your primary inbox.
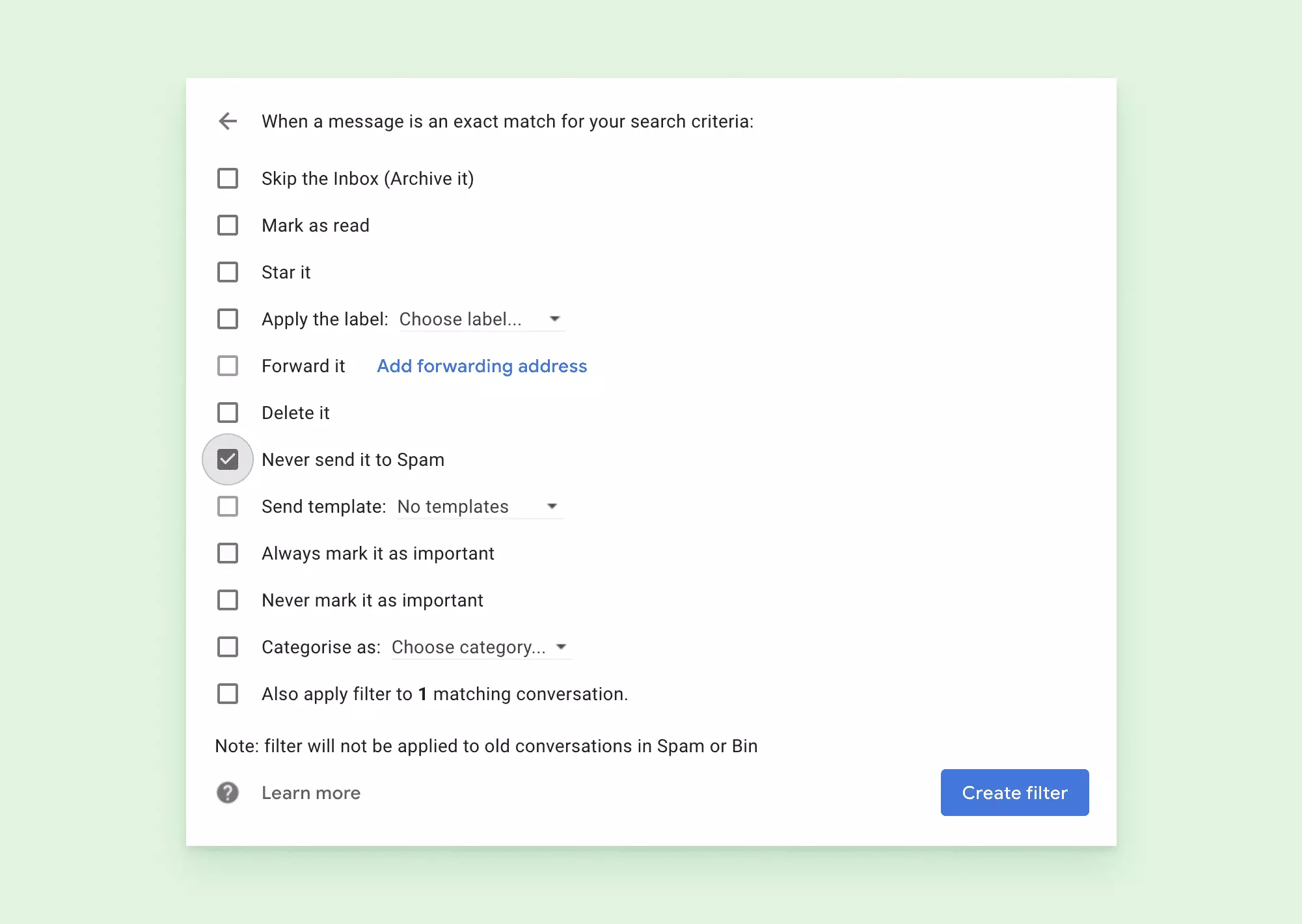
3. Create a whitelist.
Finally, if you're using G Suite Basic, G Suite Business, or Enterprise Plus, you can add senders to your allow list to safelist them by the IP address of the sending mail servers. This paid feature is worth the investment if you need to make sure follow-ups from clients and prospects never go to spam.
How to Whitelist an Email in Outlook
Microsoft Outlook has "Block and allow" settings to manage which senders you trust and which unwanted correspondence goes to your junk folder.
1. Add addresses using the Outlook-provided contacts manager.
As with Gmail, the first step is to open the contact manager provided by Outlook, and make sure that the sender is recorded there or add them. To add a sender, go back to a message from a contact you want to green-light and "Add to Outlook contacts" by right-clicking the address.
2. Curate a safe-senders and recipients list.
For this step, you need to go to Settings, then Mail, and under Options choose "Block or allow." The first way to grant access to senders is to add those contacts to "Safe senders and recipients." Another way is to select "Trust email from my contacts" to mark all your contacts as safe.
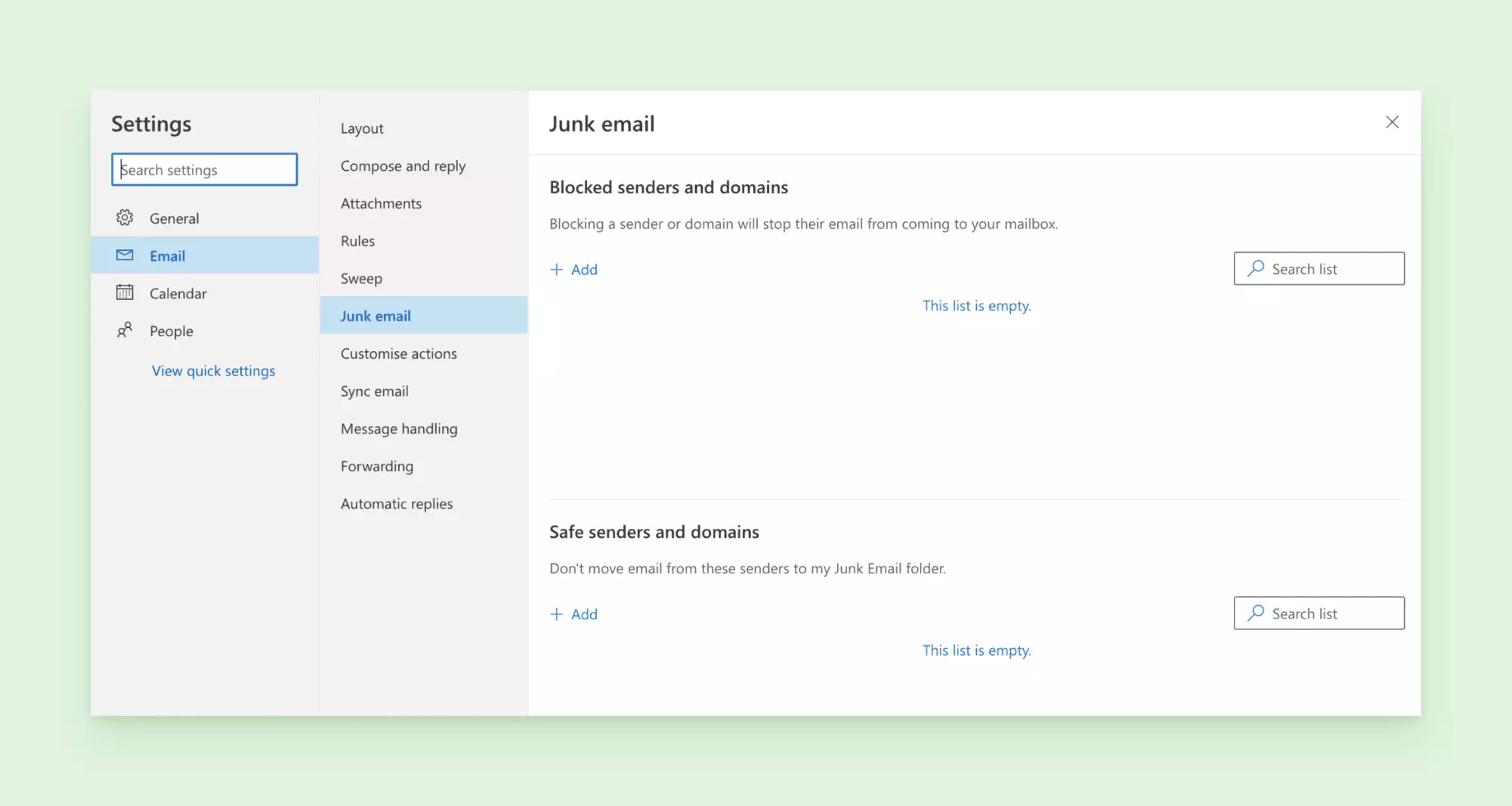
3. Check the list of blocked senders.
If the filtering system has sent a wanted message to your junk folder, you will need to unblock the sender. To do this, go to Settings, then Mail. Under Junk email, go to the "Blocked senders" list and remove the contacts you trust.
How to Unblock an Email in Yahoo
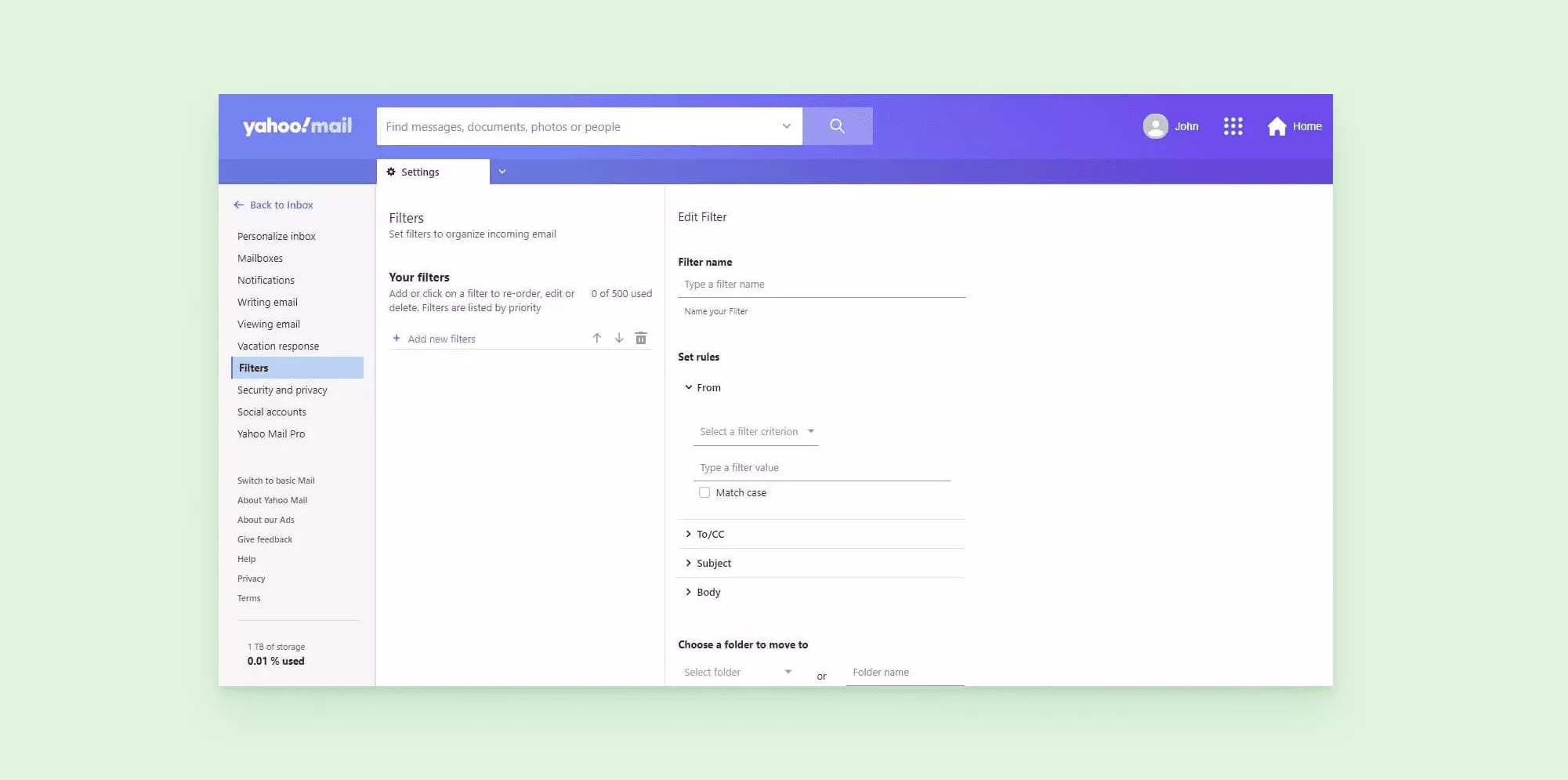
If you're a Yahoo user, the process of green-lighting email addresses is similar to that of Gmail and Outlook users. Basically, add the sender's address via your contacts manager.
From there, you can create a trusted-senders list by adding filters for specific addresses or groups and applying a rule to always send emails from them to your inbox.
Didn't Cover Your Provider?
Most providers have similar processes for creating emailing whitelists. Most commonly, adding addresses to your contacts manager and adding filters will do the trick. You can also go to your provider's support page and type in "whitelist" in the search bar to see if there's a specific feature for that, like in Google's paid service.
Conclusion: Should You Whitelist?
Whitelisting is a useful cybersecurity measure to protect your system and devices from hackers, malware, unwanted content, and rogue apps. It is more restrictive and secure than blacklisting, but it has its disadvantages. It will limit the functionality of devices and can be difficult and time consuming to implement and maintain.
The whitelist method is best for organizations that have strict data security policies. For other organizations and most users, a combination of whitelists and blacklists works best. Keep in mind that neither approach is bulletproof, and new ways to bypass the filters and protections are emerging daily.
When it comes to emails, whitelists are often the most reliable way to ensure important messages reach the inbox. Changes and updates to algorithms can be a cause of great frustration. To avoid these unpleasant situations, follow the steps above to add trusted senders to your allowed-senders list. While you're there, use the advanced options to sort emails based on your needs.
And if you want to increase productivity by managing multiple email accounts in one place, give Mailbird a try!
FAQs about Whitelisting
How does a whitelist work?
A whitelist functions as a cybersecurity list, only allowing those apps, IP addresses, programs, or email senders to communicate with you and access your systems. It's among the best practices for filtering emails and managing access to business networks, websites, and devices.
What is an email whitelist?
An email whitelist is a list of trusted contacts. Messages from contacts on this list will never end up in your junk or spam folders. With advanced spam filters and frequent updates, setting up a safelist of email senders is the only sure way to get all your important messages on time.
Is whitelisting better than blacklisting?
Both whitelisting and blacklisting are useful cybersecurity measures. The former is more strict and secure. However, it is also more demanding to set up and maintain. The latter provides more flexibility and is easier to maintain, but is also less secure. Whether you use one or the other, or a combination of both will depend on your needs.
Why is whitelisting bad?
Whitelisting itself is not a bad practice. However, it is not bulletproof. While being an excellent security measure, it can provide a false sense of security. Cybercriminals are always finding new ways to breach even the most secure systems. The more laid back you are about security, the more vulnerable you become to spam, phishing scams, and malware.
